
Using FieldShield to Comply with PCI DSS
 Abstract: Amid the still-growing problem of data breaches, and new v3 requirements of the Payment Card Industry Data Security Standard (PCI DSS) in effect, it has never been more important to protect sensitive data properly. This article examines the role of IRI FieldShield software in PCI DSS compliance and data breach mitigation through field-level application of AES-256 bit encryption and other functions.
Abstract: Amid the still-growing problem of data breaches, and new v3 requirements of the Payment Card Industry Data Security Standard (PCI DSS) in effect, it has never been more important to protect sensitive data properly. This article examines the role of IRI FieldShield software in PCI DSS compliance and data breach mitigation through field-level application of AES-256 bit encryption and other functions.
According to an Experian industry forecast, the number of data breaches will continue to rise in 2014. The average cost to a US organization is $201 for each compromised customer record (IBM 2014 Cost of Data Breach Study). With an average of 29,000 records compromised per incident, the cost of a data breach can reach well over $5 million. In addition to the significant financial obligations which result from a security breach, there is an acute loss of trust between an organization and its customers. Fallout from the Target breach comes to mind.
It is for this reason that a comprehensive data security strategy must be in place. IRI understands this necessity and provides products that will harden an organization’s security posture. IRI FieldShield technology does this by rendering sensitive information unreadable through its strong encryption, SHA-2 cryptographic hashing, and tokenization support.
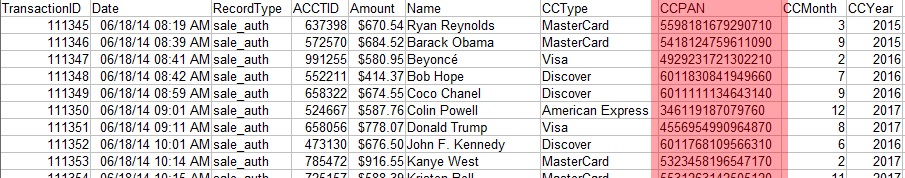
Figure 1
Pictured above (Figure 1) is an example of a transaction record table. It contains plain-text credit card primary account numbers (PANs). According to the PCI Security Standards Council, PANs should be rendered unreadable. FieldShield supports this goal in multiple ways, including data masking and redaction, as well as encryption.
FieldShield GUI users apply their choice of protection functions to PAN and other columns in an intuitive, efficient, and flexible manner under Eclipse. Specification of an encryption cipher with a passphrase would occur in a dialog that looks like this:
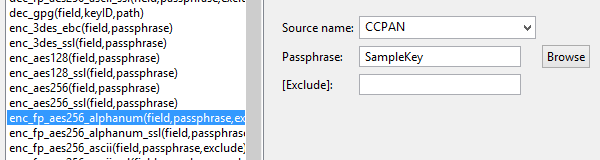
Figure 2
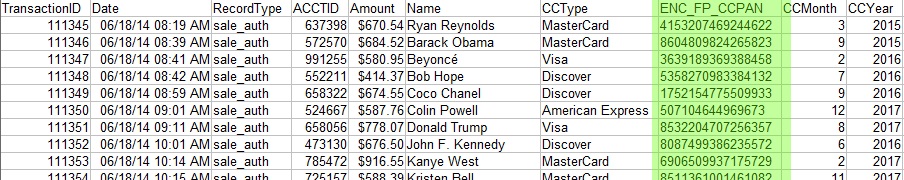
In this example, a format-preserving encryption technique is used to ensure no additional changes are required to the table or database structure, while PCI Compliance is still achieved. Read more about this type of encryption here. The result is encrypted credit card PANs (Figure 3).
Figure 3
This simple yet powerful process is important because an organization can limit the financial and operational impact of a data breach. For example, in 2011 Steam, a gaming distribution platform, suffered a data breach. As significant as the breach was, the overall impact to the Steam was limited because the credit cards were encrypted. See this article on breach nullification for related perspective.
FieldShield provides ease-of-use and peace of mind in securing sensitive data. It helps organizations meet the PCI DSS v3 requirements for protecting stored cardholder data while mitigating the risk of data loss.










1 COMMENT
As a senior PCI-QSA in North America, I actually have clients who use FieldShield and it works very well in helping with PCI compliance. With that said, i also want to add that PCI compliance can be an incredibly time-consuming and taxing challenge, no question about it. What’s important to note is that both merchants and service providers think PCI DSS compliance is all about the technical aspects – and much of it is – but they often lose sight of the fact the policies and procedures are sometime an even bigger mandate – and task – to undertake. As a QSA, one of the biggest challenges is getting clients to implement two (2) notable initiatives: (1). Undertaking an annual risk assessment and (2) implementing comprehensive security awareness training for all employees. There’s a wealth of free and cost-effective solutions online for both of these mandates, so it’s time that companies got serious about implementing such measures.