Getting DarkShield Alerts from Splunk Adaptive Response
The Splunk Adaptive Response Framework (ARF) included with Splunk Enterprise Security (ES) allows actions to be taken in response to data. This is done by creating an alert that triggers when a certain search result condition is received in the Splunk ES Search and Reporting app.
IRI DarkShield is a machine-learning-enabled data discovery and masking package for finding and securing personally identifiable information (PII) in dark data (unstructured) files — like email repositories, .pdf and Microsoft documents, and many image formats. DarkShield produces a high volume and quality of log file results from its PII search and mask operations.
By virtue of these logs, DarkShield can identify files which files it protected, versus ones that still have unmasked PII within them. You can automatically forward the logs to Splunk ES, where you can highlight key information in dashboards, and configure alerts based on specific conditions; when, for example, DarkShield found more than 3 unprotected files.
This image shows some of the alert actions that can be triggered to respond to certain conditions. These include creating Splunk messages, sending email, logging the event, and running a script.
To set up an alert, first go to “search” from the Splunk ES menu. Set the source you want to have alerts triggered from, then select the search button.
Once the search is complete, an alert condition can be generated by clicking on “Alert” from the “Save As” menu. In the picture below, my source is log.txt.
Once clicking on “Alert” a screen should appear like this that allows you to configure the conditions that trigger the alert, and what actions the alert takes.
In this case, I have the configuration set up to check every 30 minutes (based on a Cron Schedule) if there are more than 3 unmasked files from DarkShield data. The alert then triggers each time there is a file type with more than 3 unmasked files. For example, if there are 5 unmasked PDF files, 6 unmasked .doc files, and 2 unmasked XML files, the alert will be triggered twice.
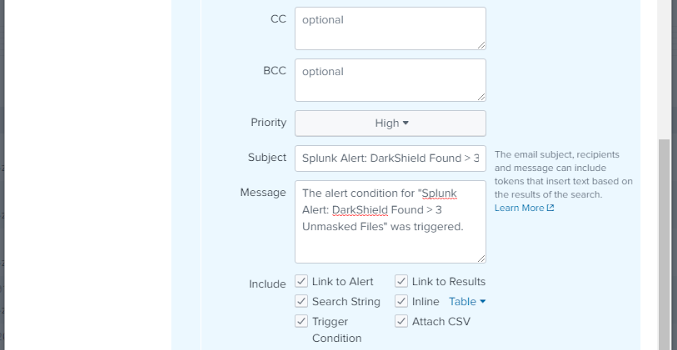
I set the alert to send an email with information about the alert, a link to the alert, the alert trigger condition and time, search condition. I also specified that both a PDF and CSV file containing a table of the particular data that triggered the alert would attach. Below you can see I also set the alert to be added to the list of high severity alerts:
Once the DarkShield user receives the email, they can respond to it by configuring, modifying, or re-running an existing DarkShield masking operation.
Splunk can also launch custom scripts when an alert is fired. IRI is developing deeper integration points for DarkShield and its other masking tools in order to support automatic remediation through this and similar mechanisms.
Meanwhile, marrying the log data from IRI Data Protector suite tools with the alert and response actions available in SIEM tools like Splunk ES can still improve the security of your data by shortening response times to those incidents you specify as needing remediation.














1 COMMENT
[…] evaluate the data that DarkShield found. Compare this to sending an alert email, described in our prior article on using the Splunk Adaptive Response Framework with […]