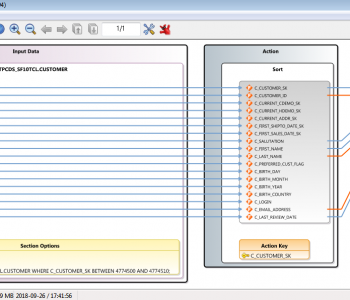
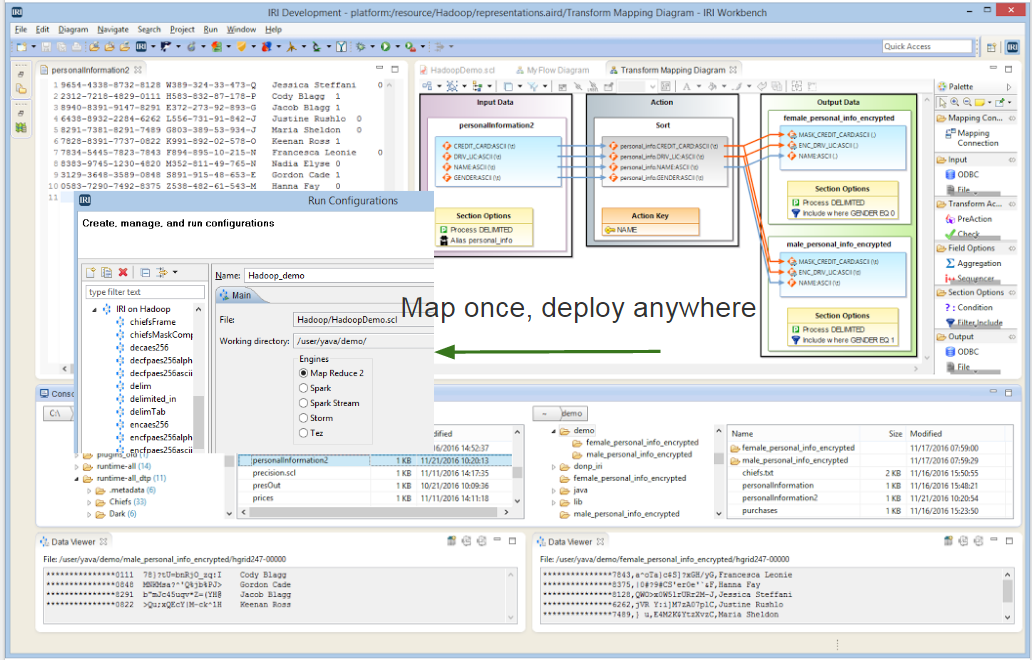
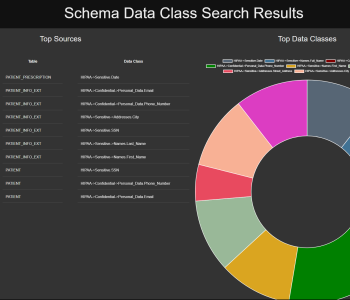
Data Masking/Protection
Data Masking/Protection
Data Security in the Business World: Navigating Challenges
Threats of data breaches and cyberattacks have intensified over the years. In 2025 alone, the total damage cost is already forecast to reach up to $10.5 trillion. Read More