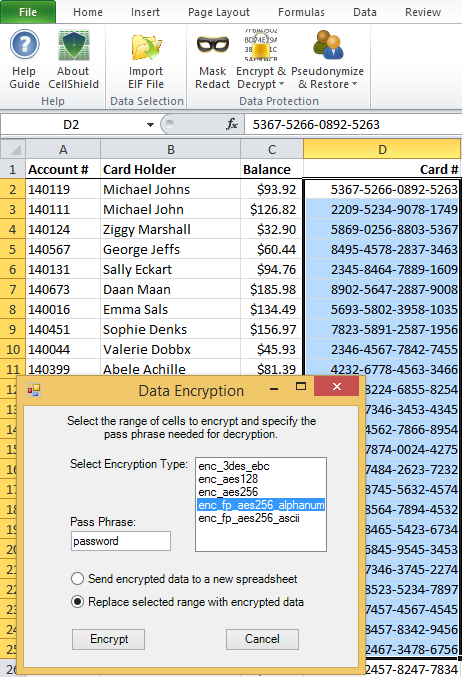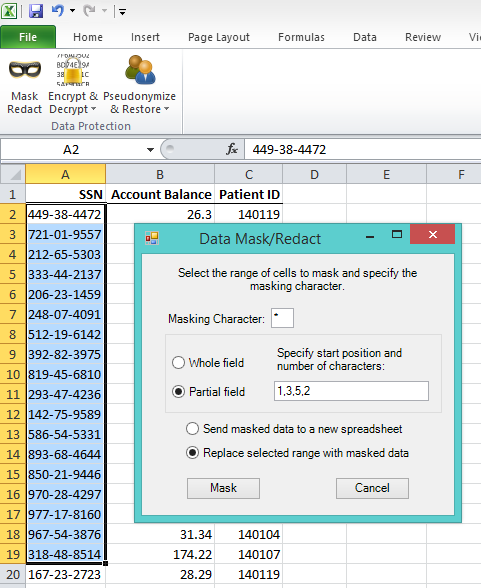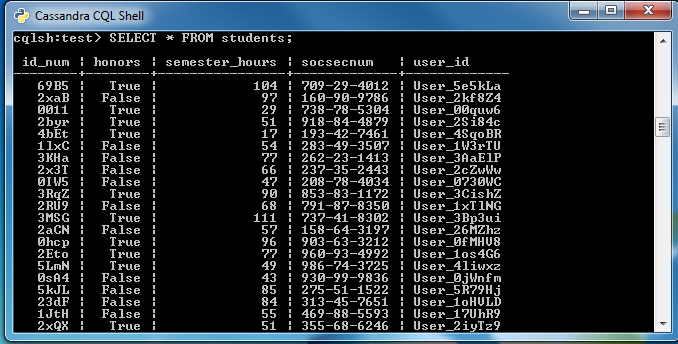
Cassandra Data Masking
Editors Note / UPDATE: The article below describes an older method of data masking in Cassandra through IRI FieldShield. As of 2023 however, the DarkShield V5 features a purpose-built NoSQL DB API for searching and masking operations in Cassandra, as well as fit-for-purpose graphical wizard in the IRI Workbench GUI for DarkShield that leverages the API for PII protection in Cassandra. Read More