IRI DarkShield RPC API
Editors Note: The article below was written prior to the release of V5 of the IRI DarkShield PII data masking tool for structured, semi-structured, and unstructured data. Read More

Editors Note: The article below was written prior to the release of V5 of the IRI DarkShield PII data masking tool for structured, semi-structured, and unstructured data. Read More
Like previous articles in this blog on the connection and configuration of other relational databases with the IRI Voracity data management platform — and its ecosystem products: CoSort, NextForm, FieldShield, DarkShield and RowGen — this article details how to reach DB2 sources. Read More
IRI Workbench now contains a section of data cleansing, enrichment, and validation rules called Data Quality Rules for use in IRI CoSort data transformation and IRI Voracity ETL, reporting and data wrangling jobs. Read More
Whether your SQL Server database is on-premise or in a cloud enviroment like Azure, its data is accessible for movement and manipulation in IRI Workbench-supported products like CoSort, FieldShield, DarkShield, NextForm and RowGen, or the IRI Voracity platform which includes them all. Read More

Abstract: This is the second of a two-part series detailing data class validation in IRI Workbench. The first article, here, provides an overview of the validation scripts and how to use them in a data discovery or classification job. Read More

Abstract: This is the first of two articles on data class validation in the IRI Workbench graphical IDE for the IRI DarkShield, FieldShield and CellShield EE data masking tools. Read More
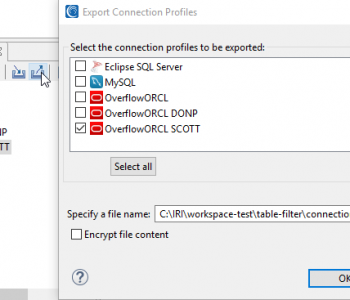
IRI Workbench provides a number of features for working across multiple tables in a database. It includes wizards to: profile databases; classify columns; subset, mask and migrate data; generate test data; etc. Read More
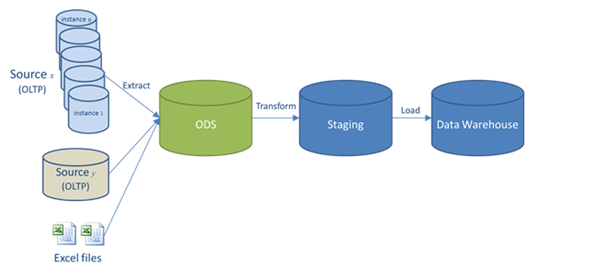
An operational data store (or “ODS”) is another paradigm for integrating enterprise data that is relatively simpler than a data warehouse (DW). Read More
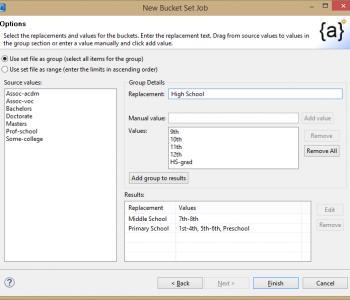
Editors Note: This articles covers data anonymization as a form of data masking for privacy protection. In particular, it covers the concepts of quasi-identifiers and re-identification risk and the use of HIPAA data de-identification standards for protecting sensitive data in research through the use of anonymizing techniques like age blurring and demographic attribute blurring in conjunction with re-ID risk scoring. Read More
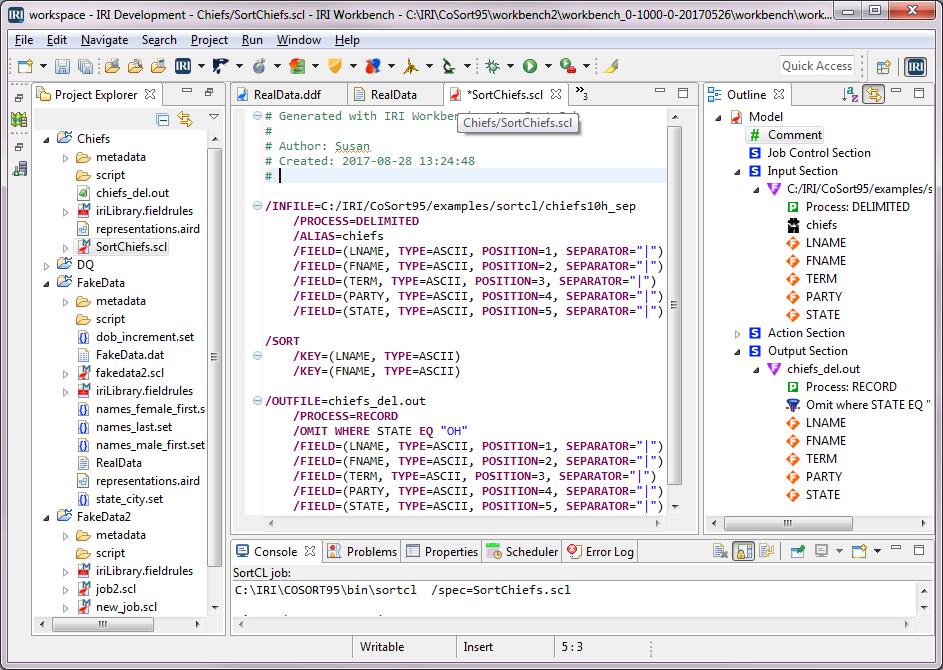
The IRI Workbench GUI, built on Eclipse™, provides several ways to create data-driven jobs … jobs which are ultimately expressed in self-documenting plain-text scripts and metadata files. Read More
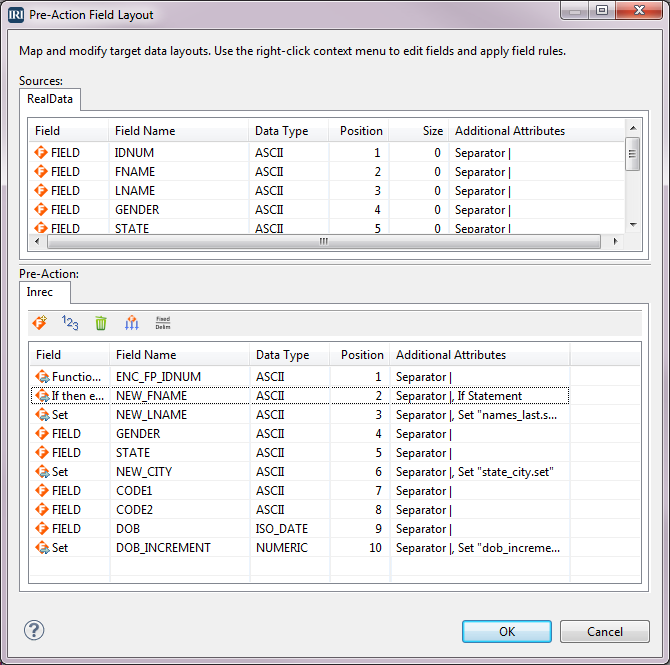
There are times when it is necessary to test with or share data that has elements of personally identifiable information (PII). To comply with data privacy laws and prevent a data breach, you may need to provide data that reflects, and sometimes imparts, critical information, but still protects the PII. Read More