Managing and Masking SharePoint Data with Voracity
This article explains how to connect with, and use data from, SharePoint sites — using the file system via OneDrive — for operations in IRI Workbench-supported data management software. Read More

This article explains how to connect with, and use data from, SharePoint sites — using the file system via OneDrive — for operations in IRI Workbench-supported data management software. Read More
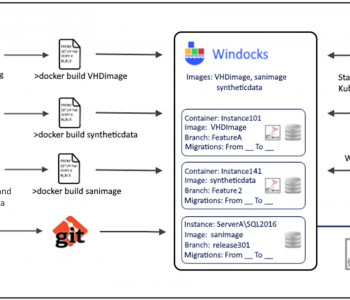
Abstract: IRI has partnered with Windocks to provide an on-demand, test-ready virtualized repository that delivers masked, subsetted or synthesized databases in seconds for Docker containers, conventional instances, or workstations. Read More
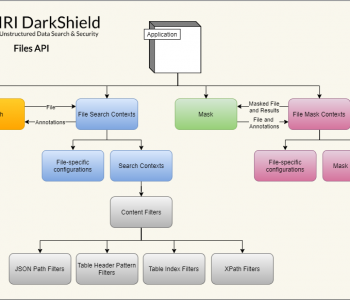
The IRI DarkShield data masking tool features a self-hosted (on-premise) Remote Procedure Call (RPC) Application Programming Interface (API) for searching and masking data in structured, semi-structured and unstructured files. Read More
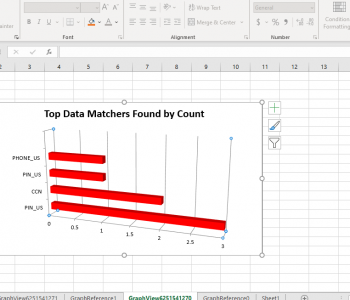
IRI CellShield® is an add-in for Microsoft Excel® that protects the sensitive information in one or more spreadsheets, allowing you to comply with data privacy laws and nullify data breaches. Read More

Forty years after the first release of IRI CoSort for CP/M, CoSort v10 for Unix, Linux, and Windows platforms was released in the middle of 2018. Read More
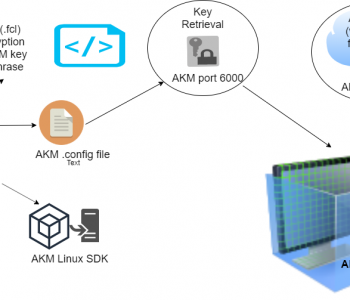
In a previous article, we detailed a method for securing the encryption keys (passphrases) used in IRI FieldShield data masking jobs through the Azure Key Vault. Read More
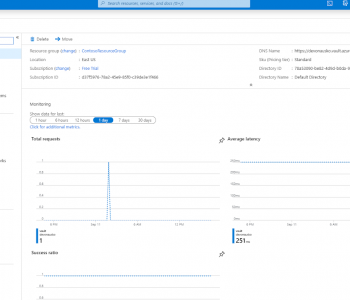
Abstract: This article covers Azure Key Vault encryption key management as part of data encryption best practices. It explains how to use Azure Key Vault and how to perform secure passphrase storage in Azure for encryption and decryption in the IRI FieldShield data masking tool. Read More
In Q3’19, IRI created a new, free app for Splunk Enterprise and Enterprise Security users that seamlessly indexes data from any Voracity platform data wrangling or protection job. Read More
KNIME is a leading open source analytic and visualization tool for data scientists. Wrangling raw data for KNIME projects is usually done via their intermediate file node, database connectors, or other extensions like Spark. Read More

Article 17 of the General Data Protection Regulation (GDPR) stipulates the need to minimize aging data through deletion, as well as the ad hoc Right to Erasure, often referred to as the Right to be Forgotten. Read More
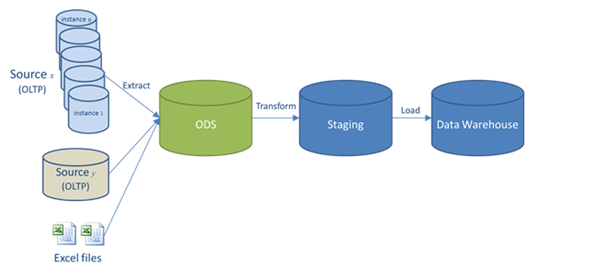
An operational data store (or “ODS”) is another paradigm for integrating enterprise data that is relatively simpler than a data warehouse (DW). Read More