 Data Masking/Protection
Data Masking/Protection
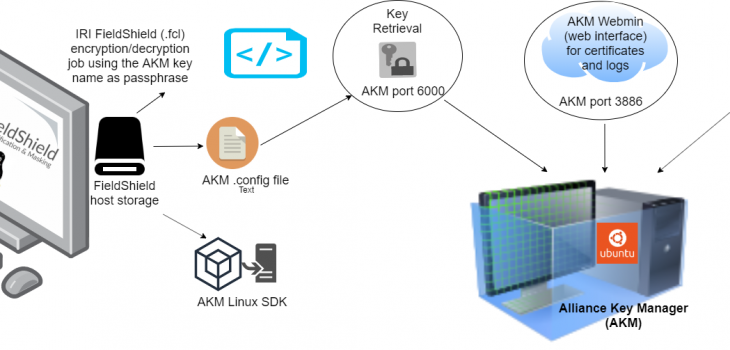
Securing FieldShield Encryption Keys with Alliance Key Manager
In a previous article, we detailed a method for securing the encryption keys (passphrases) used in IRI FieldShield data masking jobs through the Azure Key Vault. Read More