Data Masking/Protection
Data Masking/Protection
Data Class & Rule Library in IRI Workbench
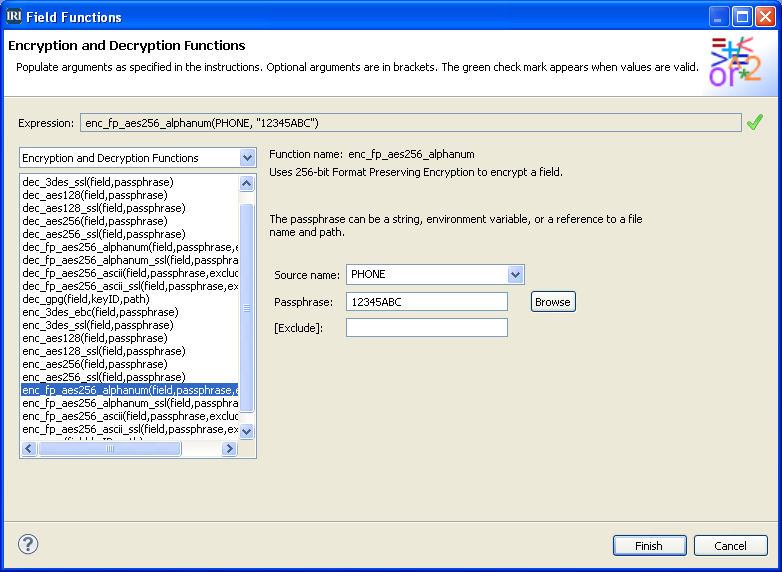
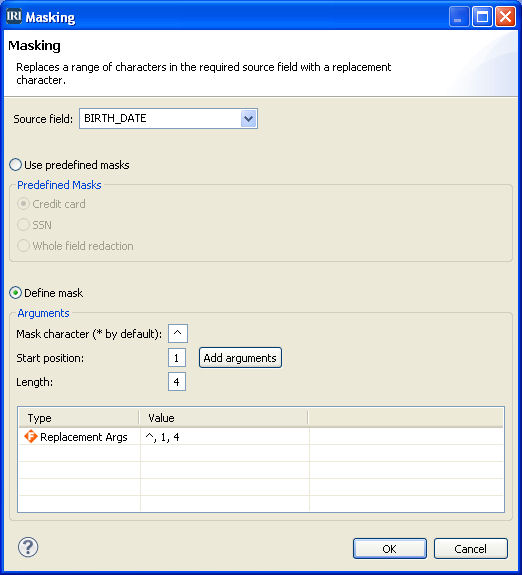
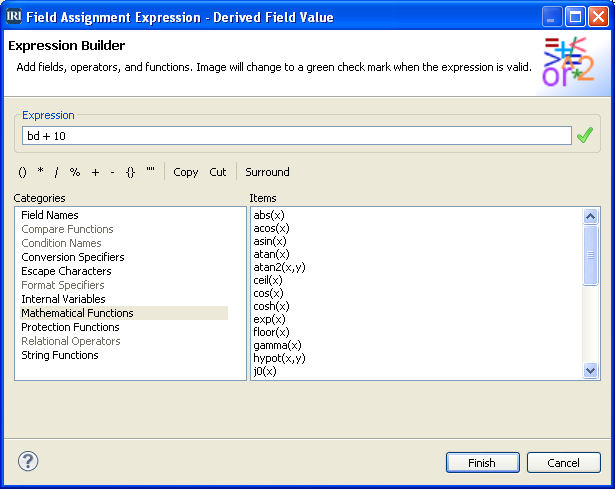
Abstract: HIPAA, GDPR, FERPA, and other data privacy laws require that personally identifiable information (PII) and related data considered sensitive be protected from disclosure or discovery. Read More