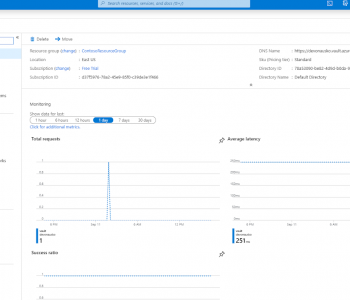
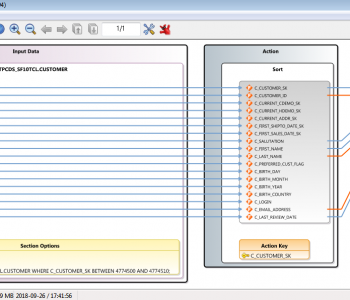
Big Data
Big Data
Masking & Mapping Data in a Snowflake Database
Finding and masking personally identifiable information (PII) in Snowflake® data warehouses works the same way in IRI FieldShield® or Voracity® installations as it does for other relational database sources. Read More