 Data Masking/Protection
Data Masking/Protection
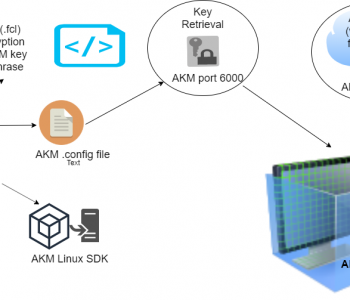
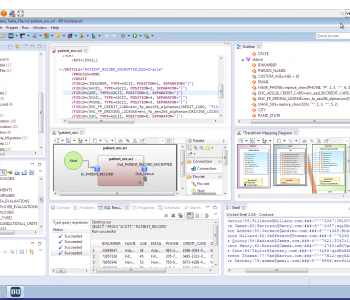
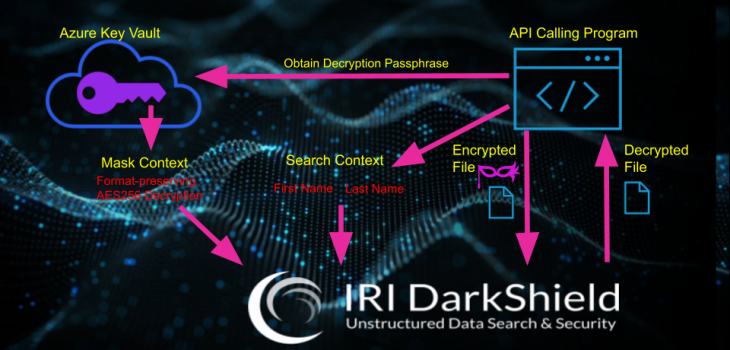
Restoring Masked Values with IRI DarkShield
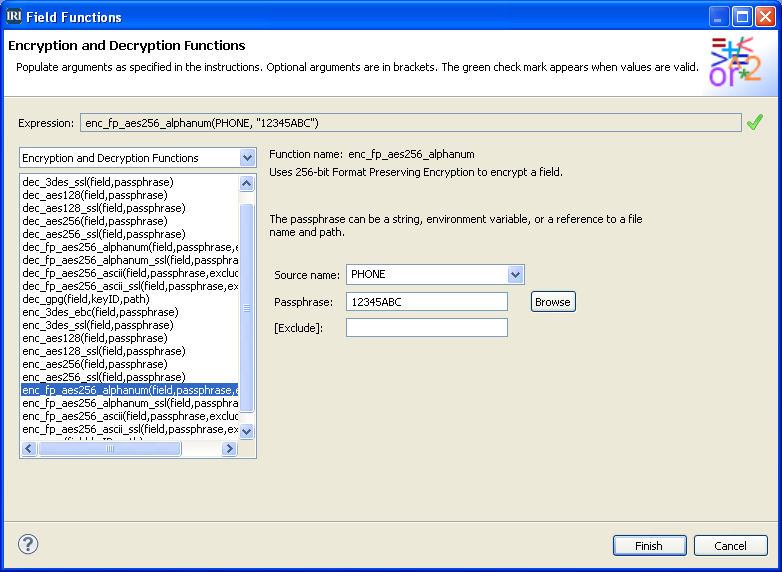
IRI DarkShield data masking software focuses on discovering and masking sensitive data in a wide variety of sources, including unstructured and semi-structured files, documents, and databases. Read More