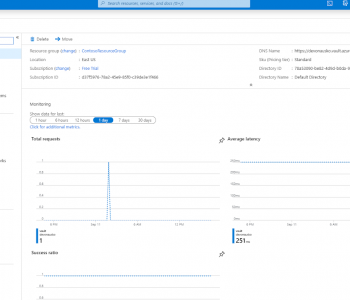
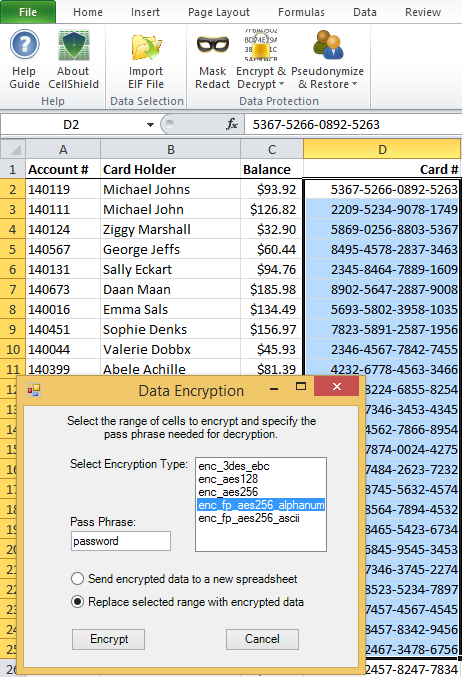
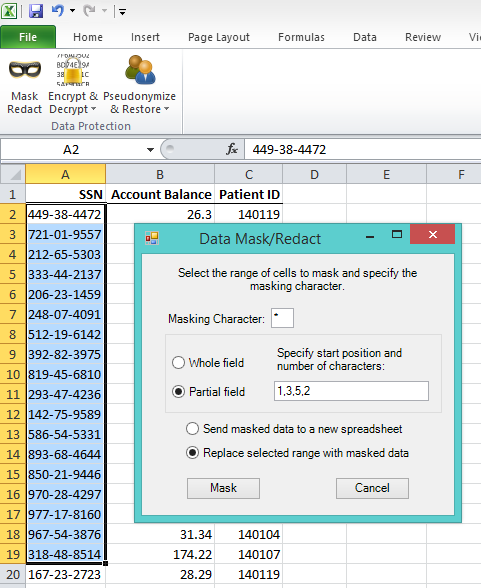
Data Masking/Protection
Data Masking/Protection
Oracle TLS Support
To configure both JDBC and ODBC to support the Transport Layer Security (TLS) protocol, there are additional configuration steps that are needed when compared to this previous article. Read More