 Data Masking/Protection
Data Masking/Protection
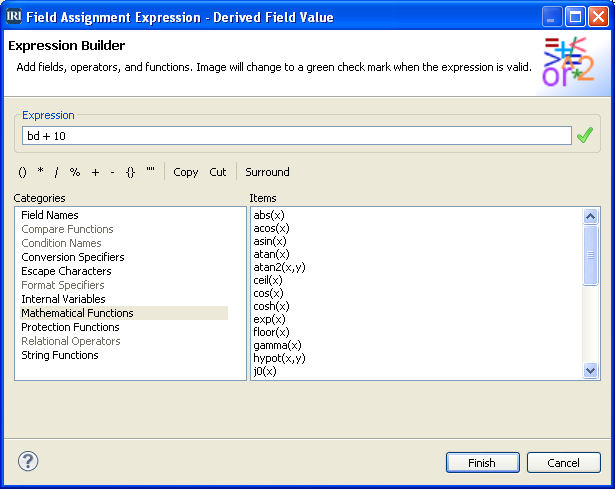
Data Masking: Obscuring Dates and Ages
Editor’s Note: Note that this article refers to older but still supported methods for obfuscating PII elements like dates of birth and ages in IRI FieldShield. Read More