The categories below are broadly named in the interest of space. Please explore the Solutions section of this website and, in particular, Data Governance and Data Masking for more information.
Data-Centric Security
Data represents risk. What are you doing to protect the personally identifiable information (PII) and master data in your databases and files? Are your security practices cumbersome or heavy-handed? Are you laboriously trying to strip out sensitive data or cutting off access to entire files, databases or disks, just to protect one or more field values like a social security number? How separate, costly, or time-consuming are these tasks?
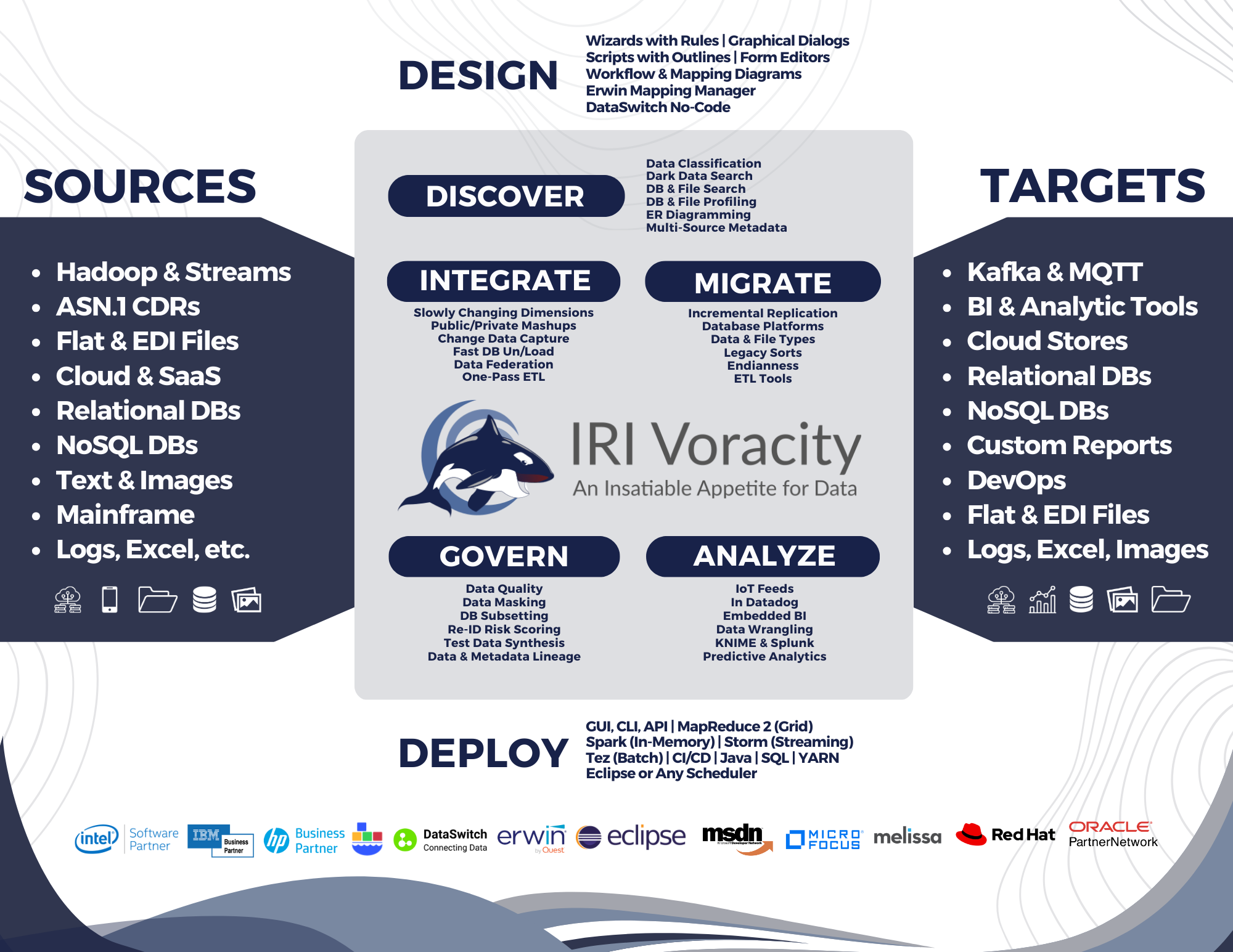
With tools in the IRI Data Protector Suite like FieldShield, DarkShield, and RowGen, you can classify, discovery, mask, risk-score, and anonymize PII, as well as subset and synthesize safe test data. And with the larger IRI CoSort package or IRI Voracity platform for 'total data management', you can fold data masking into data transformation, migration, cleansing, replication and reporting operations:
Read more about IRI's integrated, targeted, and auditable security functions for data on-premise or in the cloud:
In addition to field-level privacy protections, IRI tools can help you create safe, referentially correct test data for databases and flat files, as well as reports in custom formats. Read more about rapidly creating test data with the appearance and intelligence of production data, but without any of the risks:
Either way -- through the protection of real data or the generation of realistic data -- you can render data in tables and files safe for compliance and outsourcing.
Broader Data Governance
Effective data governance goes far beyond the security aspects of data stewardship. See these links if you are interested in how IRI software addresses:
- Metadata & Master Data Management
- Customer Data Integration & Segmentation
- Metadata Preservation
- COBIT Support
It's not enough that your software and systems can map, transform, report, and protect your data. You may need to examine or prove what was done, when it was done, where it was done, and by whom. See how we can help you with:
Data Processing Forensics
Dramatic changes in data values or record counts can also be red flags that need to be caught automatically. CoSort or Voracity job scripts, output reports, and log files can help you filter, capture, display, and record data changes during batch runs through large files. For specifics, see:
IRI's white paper, called "Making Data Safe for Outsourcing and Compliance," also describes the challenges and solutions on this page, and lists how IRI tools map to 24 of COBIT's 34 control objectives for good IT governance. Ask for it.


