Challenges
You need to remove the personally identifiable characteristics of data. At the same time, that data needs to be individualized so it can flow safely de-identified through different departments and, where necessary, be re-identified.
De-identified data should also resemble its original format. Its length, data type, or even a real-looking but different value is needed for ongoing operations and testing. Field encryption does not accomplish this goal when the ciphertext length exceeds the original field length, and data realism is lost.
The format-preserving encryption (FPE), or format-preserving scramble functions, on the other hand, can be desirable options, though in some cases may be overkill or time-consuming.
Solutions
The IRI FieldShield data masking product (as well as the IRI Voracity data management platform which includes FieldShield and DarkShield) includes many static-data masking functions, including the ability to "roll your own." Among the built-in functions to de-identify ASCII data is a character-level twiddling or bit manipulation routine to replace values (formerly referred to as the ASCII de-ID and re-ID function)
You can use this less secure data scrambling function when speed is of the essence, and you simply want to obfuscate the column value in a unique and recoverable way.
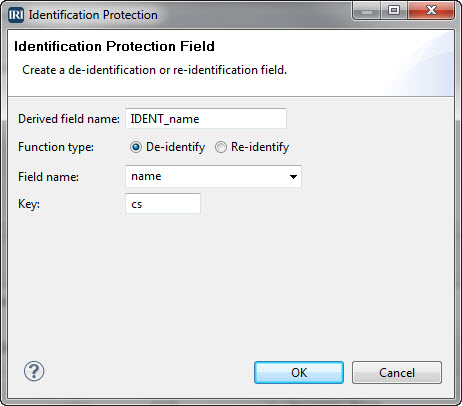
ASCII De-ID: One of several data masking function dialogs in the IRI Workbench GUI for FieldShield, built on Eclipse™.
Like the other field-level de-identification methods in FieldShield, this function can be applied to less sensitive, but perhaps quasi-identifying data, to help you comply with data privacy regulations, while leaving your non-sensitive data available for further processing. This use of this function, like all the others, gets recorded into FieldShield\'s XML audit log to help you verify compliance.
See the other functions tabbed across this section if you are looking for other ways to de-identify data. See the HIPAA page on PHI de-identifcation, and our dynamic data masking capabilities.
If you need safe, realistic test data, use FieldShield-compatible IRI RowGen software in the IRI Data Protector suite to create test database, file, and report targets.


